The Role of Artificial Intelligence in Cybersecurity
Artificial intelligence (AI) is revolutionizing the field of cybersecurity by enhancing the capabilities of organizations to detect and respond to cyber threats.
Apple’s M-series Chips: A Threat to Your Crypto Wallet
The Security Flaw in Apple’s M-series Chips: A Threat to Your Crypto Wallet As the value of cryptocurrency continues to rise, it’s vital to stay …
Overcoming the Challenges of Cybersecurity Training
As cyber threats continue to evolve and grow in sophistication, the need for cybersecurity training has never been more pressing.
The Elephant in the Smart Room: Cybersecurity Concerns with IoT Devices
In this article, we will discuss the state of IoT, and address security issues that come along with IoT devices.
Market Research in the Cybersecurity Space, PeerWise in 2023
The cybersecurity industry is continually growing. The global cybersecurity market is projected to double from 2022 to 2029. Being able to recognize new security trends, research these trends, and then analyze the findings allows businesses to be at the forefront of a quickly evolving market. Vendors, security professionals, and business owners all benefit from up-to-date cybersecurity data. Luckily, the market research industry is seeing exciting developments that position PeerWise to offer quick and accurate research results. In this article, we will discuss the state of market research, and how market research will play an increasingly important role in the cybersecurity space.
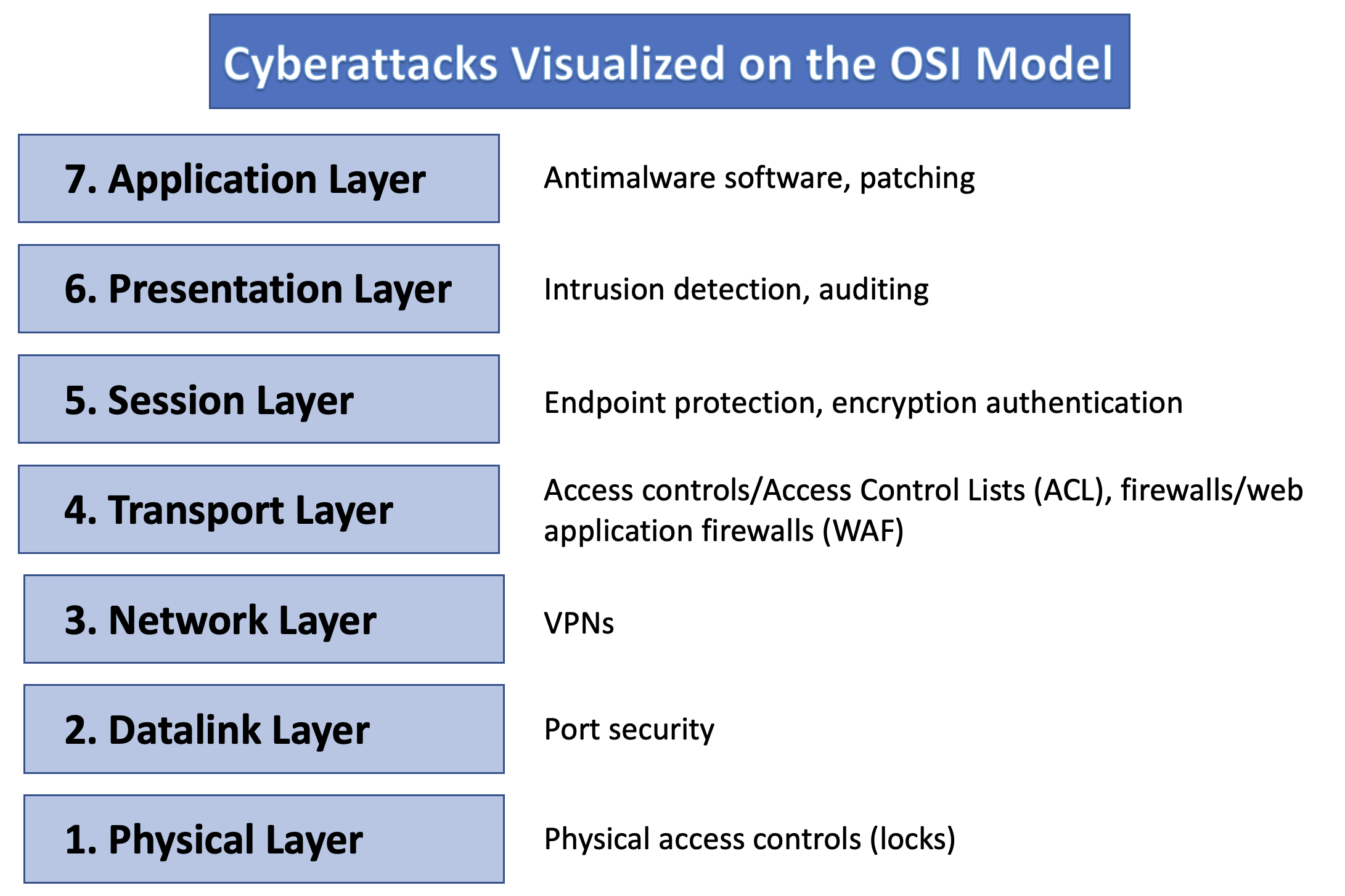
Relating the OSI model to cybersecurity
As a follow-up to our recent article introducing the Open System Interconnection (OSI) model, we will be going into detail on looking at the model through a cybersecurity lens. Understanding what protocols are targeted in network communication will allow you to best implement security to protect from these attacks. In this article, we will discuss how the OSI model can be used to understand both cyberattacks and the cybersecurity measures that can be used to protect from these attacks.